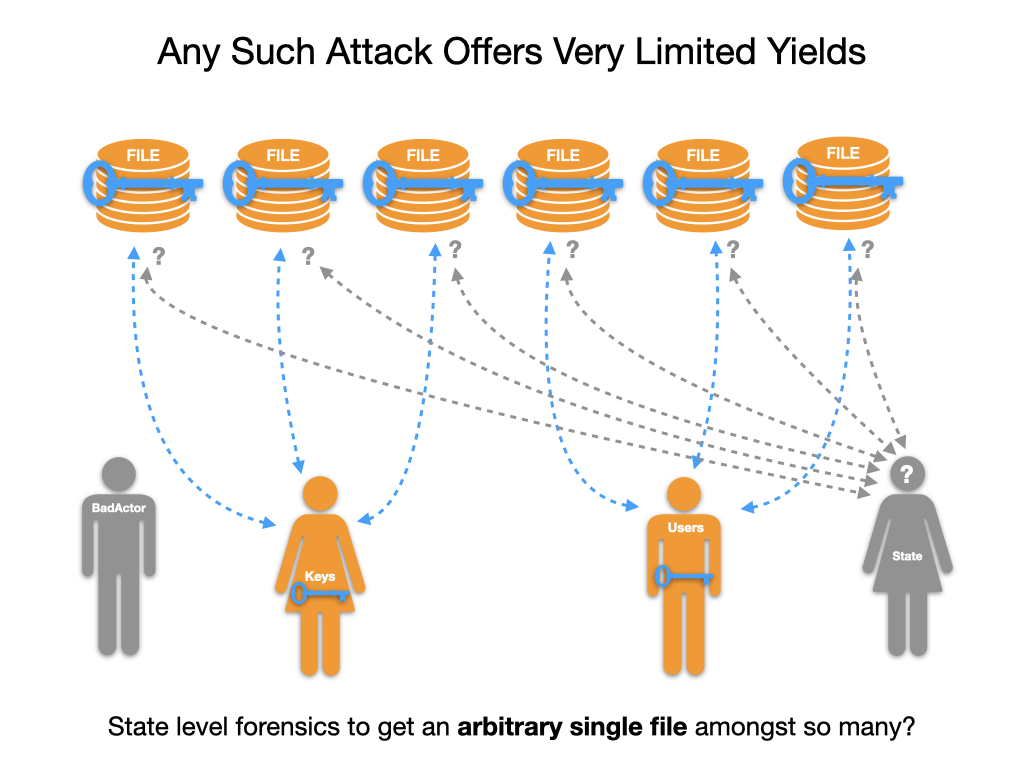
Security attacks offer
Limited Yields
SOVEREIGN SILOS EXPLAINED / NEXT
Even state level forensics offers a very shallow yield. From such conspicuous behaviour.
Trying to compromise any/all of users' silos creates a distinct footprint - back to perpetrators. For a single arbitrary file?